
As a curious technologist, one of my first thoughts after welcoming a digitised driving license is how hard would it be to fake this? I decided to reverse engineer the licence to find out.
Service NSW recently released a digital license for all license holders. This was previously a limited trial, but despite a quiet release, there have already been over 600,000 people create their digital licences.
As someone who has been gradually carrying less and less cards around, the digital option is a welcome change. I’ve already stopped carrying my bank/credit cards as well as most reward cards, this is a nice step towards digitisation.
In an ideal world digital IDs are harder to fake than physical ones, and I sought out to understand how the digital license worked, and what measures were in place to prevent faking a digital license.
The obvious measures taken to protect the integrity of the platform are visually apparent. There is a timestamp and several animations, one which changes as you move the phone around. These stop any attempts at using a photo or altered one as a license, but is it enough?
A capable mobile engineer could throw together a version of this license in a week or two, the digital hologram might be tricky to replicate precisely, but reverse engineering the Service NSW app should yield most of the code for the animation.
Fortunately the security measures don’t end there. The digital license feature includes a QR code which changes every once in a while, and seemed sufficiently complex to hold a lot of information.
I started to realise that the only real way to prevent a license from being faked or duped lies in the verification process, which is why the license is using the QR code to start with.
News reports on the digital license mentioned that police and certain venues have a way to verify the digital licenses, so I set out to understand just how that all works.
I scanned several of the QR codes for my license from the app, and set out to decipher how it works.
The QR code contains a seemingly random set of strings, separated at times by full stops. When I compared some of the different codes, I noticed that the series of characters after the final full stop only changed the last few characters for QR codes that were generated a short time apart. This lead me to believe that the code contained information that was encoded using base64, a common method of encoding special characters into a simpler set of characters (only numbers and English letters).
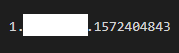
Sure enough, decoding part of the code after the final full stop resulted in my license number and what I verified to be a UNIX timestamp of when the license was generated.
So far I hadn’t seen anything that couldn’t easily be forged, so I decided to keep digging. My next target was the long set of characters that were at the start of the code, immediately after a “1.”. Once again I use the same method of decoding the characters, this time resulting in a JSON object (JavaScript object notation).

The JSON object contained 5 attributes. 2 of them were simply set to 1, another was the time stamp previously decoded, and the other 2 were seemingly random. One of the attributes looks a lot like a GUID (Globally unique identifier), which is a set of characters separated by dashes, often used as a unique identifier for a record in a database. The final attribute proved to be a digital signature, potentially a PGP signature.
This is where my investigation ended given my high level of confidence around finding a digital signature which through cryptography verifies authenticity. All it would take to verify the QR code of a license is a QR reader app than can process and display the data, as well as holds the public key allowing the verification of the signature, which would prove the data in the QR code was generated by the correct authorities.